



STRAIGHT 2 WORK TECH, LLC

813 770-6082


We accept the following forms of payment:cash, Paypal, Zelle, check, and credit.

Commercial and Residential technical service company
located in South Hillsborough County, near Tampa, FL.
Remote and on site work provided by licensed and experienced technicians. Call today to schedule an appointment!!


Don’t use the same password for every site you visit.
Using the same password for all of your online accounts such as banking and email is essentially using the same key for your car, home, office, gym locker…. All it takes is for one of those keys to be taken and a criminal will have access to every part of your life. Same with a password, if a hacker breaks into your email account and steals that password, they will have access to every other account you have online. It may seem like a lot of work, but it is a lot less work to use a unique password for each account then it is to deal with being hacked.
Use long complicated passwords that include upper and lower case letters, numbers and symbols.
The longer and more complicated your password is, the harder it is for someone to guess or crack. According to Norton, the top 5 passwords from 2013 were: 123456, password, 12345678, qwerty and abc123. This is incredibly alarming considering the large amount of people online that use the same password for all their accounts. Using a password like “S$bi@B&nuhM” would be a lot harder to crack then 123456. Of course trying to remember that password would be incredibly hard, and even more so when you use a different password for every site so you could use a phrase to remember the password such as “Sam’s money belongs in a bank and not under his mattress”. Another method to keeping track of all these passwords would be using a password manager.
Use a password manager to keep track of all your unique passwords online.
Password managers are fast becoming the go to online password solution to keep all of your passwords safe and secure. A password manager works as a central database of all your login sites, usernames and passwords. You remember a single password to access the manager so when logging into your bank and Facebook you only have to remember the one password for your manager while still using complex and unique passwords for both logins. This saves a lot of time and headaches in the long run. Setting up a password manager such as LastPass 3.0 can be time consuming depending upon the amount of websites you log into on a frequent basis, but will ultimately save you time overall.
Set up 2 step authentication for your logins.
Two step authentication is the process of having you sign in as you normally would with your username and password but then sends you a custom code, usually numeric to your cell phone via text or a phone call or to your email. You then have to enter that code before you are able to access the site. Almost all large companies and banks offer a 2 step authorization login and it is highly recommended.
Change your passwords every couple of months.
Every two or three months you should change all of your passwords just to ensure that they have not been compromised. Again, this may be a bit time consuming but it will be well worth it if anything should happen in the future.

In today’s ever evolving online presence, passwords are the first line of defense in protecting ourselves and our information. From online banking and emails to social media and online shopping sites, every one of them require a password. With cyber criminals and hackers accessing more and more of these sites databases through security holes such as the recent Heartbleed exploit, people’s passwords are being stolen very frequently. Most recently eBay announced that the personal data of 145 million customers was stolen, including passwords. So how can you make sure your data and personal information stays safe when things like this happen?




ALWAYS VERIFY WEBSITE BEGINS WITH HTTPS:
-
Encryption—encrypting the exchanged data to keep it secure from eavesdroppers. That means that while the user is browsing a website, nobody can "listen" to their conversations, track their activities across multiple pages, or steal their information.
-
Data integrity—data cannot be modified or corrupted during transfer, intentionally or otherwise, without being detected.
-
Authentication—proves that your users communicate with the intended website. It protects against man-in-the-middle attacks and builds user trust, which translates into other business benefits.

Every computer must run some core software known as an Operating System, or OS for short. The three most common OS’s are Windows (of multiple versions), Mac, and Linux.
Malicious software, or malware for short, is broken up into several categories. These are virus, Trojan, and worm for example, and they can serve many purposes. Each malware is classified by the method it uses to infect and spread. A virus is actually quite rare anymore, and infects by attaching itself to an otherwise harmless file, and then spreading to other files as they’re opened. A worm actively seeks to exploit open vulnerabilities to spread itself to other computers, but doesn’t infect files themselves. And a Trojan generally infects by pretending to be something harmless. For the most part, Trojans are the most frequently encountered form of malware on the internet, and for a good reason. They prey on most people’s inability to distinguish fake malicious programs from legitimate ones.
The first method of infection is by website scripts that pop up fake, but very realistic-looking windows warning you of problems with your computer. These are generally designed to look nearly identical to popular antivirus warning windows. Usually they are written in such a way that clicking anywhere in the window at all, even in some cases clicking the X to close the window, instead gives the software permission to download and install itself. The best way to avoid this sort of attack is to kill the window entirely without clicking in it. You can do this either by going to task manager (pressing ctrl-alt-esc, all at the same time), finding your browser, and choosing End Task, or by possibly just closing the window by pressing Alt-F4 or Ctrl-W (these combinations work in most browsers and all versions of Windows). If you do end task on your internet browser and the threatening window is still there, either it’s still running as a separate browser (look for more copies of Internet Explorer, Firefox, or Chrome), or it’s not running in the browser anymore. In these cases, either it’s legitimate (your antivirus really is stopping it), or it’s already managed to get a foothold on your computer and the start of an infection. In these cases, it’s generally best to let a professional take over. If it goes away, you’re likely ok. However, if you start getting strange windows and programs later, its best to get it looked at and cleaned by professionals.
The other method for infections to occur is by pretending to be something that would entice users to download it, such as a free game, or a free utility that claims to be able to make your computer run better or faster somehow. Any of these types of utilities that you run will claim to find numerous problems with your computer, but also claim to be unable to fix them without “upgrading” to a paid version of the software. For the most part, these programs tend to be either truly malicious in some cases, or simply ineffective in the case where they are not malicious. There are a few exceptions, however, but that’s, again, outside the scope of this article.
Generally, your safest bet is to install a legitimate and well-known antivirus software program (after checking reviews and feedback to ensure that it’s effective), that helps flag known malicious websites. Most antivirus packages do this in some way when you are searching online via Google or Yahoo or any of the major search websites. Avoid clicking on suspicious links, avoid downloading software that sounds too good to be true, and above all, make sure your security software is updated on a daily basis.
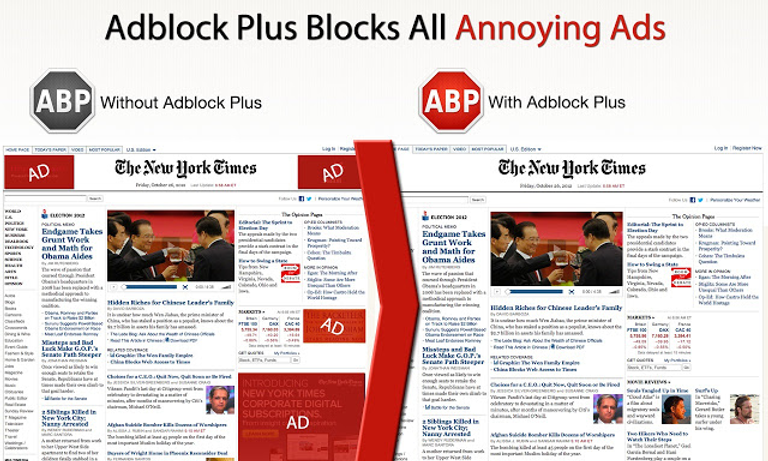
This brings up the final point. NO antivirus program is going to be 100% effective. Every antivirus works from a database of known malware, and small variations can mean that something goes undetected. New variations are released every single day in order to try to get around an antivirus’s shields. If you find yourself infected despite up-to-date protections, it isn’t necessarily the fault of the antivirus. Sometimes it just doesn’t have that infection in its database yet. A great preventative measure is to install a pop up blocker to your browser. Adblock Plus (ABP) is an open-source content-filtering and ad blocking extension for Mozilla Firefox, Google Chrome, Internet Explorer, Opera, Safari, and Yandex Browser web browsers.

